How to Configure RADIUS Authentication on Cisco Switch
- Last updated: Apr 10, 2025
Introduction
I've talked a lot about how to implement the RADIUS authentication in WiFi (a.k.a WiFi Enterprise) in a Microsoft environment. You can read this wonderful tutorial: How to Deploy WPA Enterprise EAP-TLS on UniFi WiFi.
But what about network cable connections? What if we want to protect physical access too? An attacker could easily gain access to the corporate network by connecting directly to a switch. So I'm going to show you how to authorize only identified devices to access the corporate network.
- I have tested this configuration on the following switches:
- Switch model: Cisco SG550X
- Switch model: Cisco SG350X
- Switch model: Cisco CBS250
- Switch model: Cisco Catalyst 1300

Configuring NPS
I'm not going to detail the whole NPS installation process here, as I've already explained it here. I'll just show that we need to add the IP address of our switch so that it can communicate with our NPS server.
- Open the Network Policy Server console:
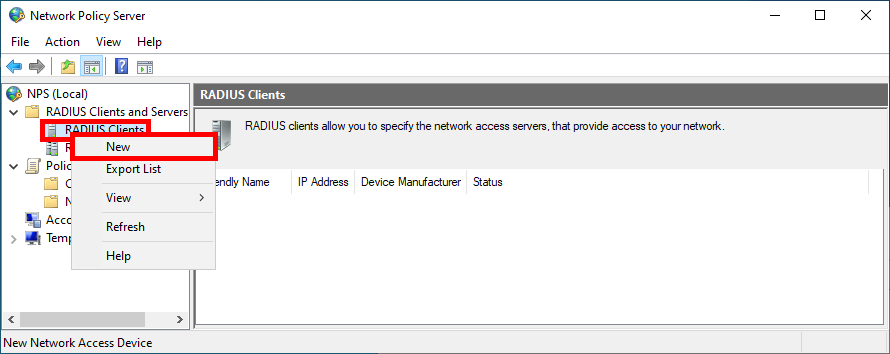
- Navigate to NPS > RADIUS Clients and Servers > RADIUS Client and click New:
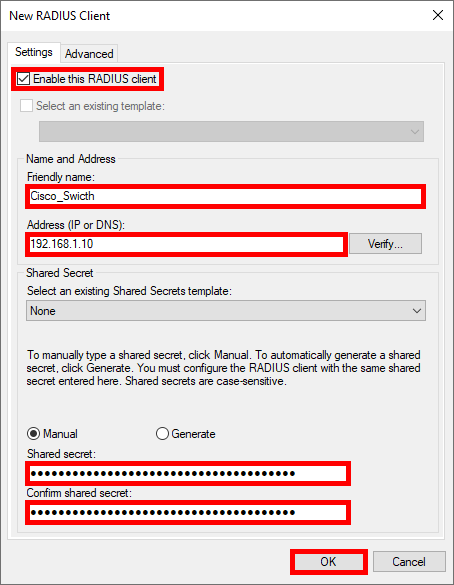
- Give it a Name, set the IP address and create a strong password to be shared with the switch (see below):
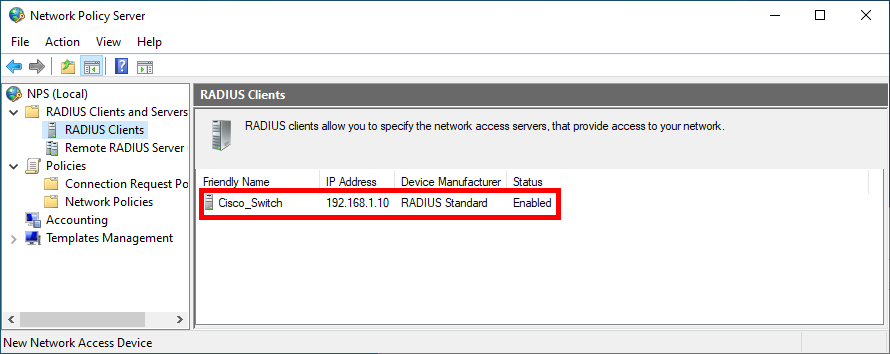
- Once validated, you should see the Cisco_Switch entry in the RADIUS Clients folder:
Windows client workstations
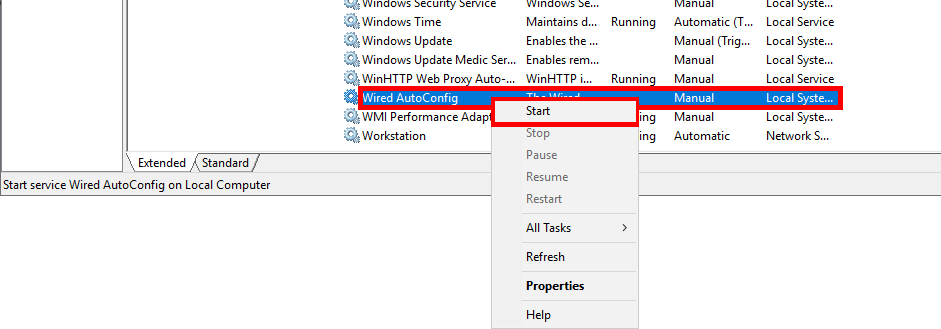
On Windows client workstations, we first need to start the Wired AutoConfig (dot3svc) Service. This service is responsible for IEEE 802.1X authentication on Ethernet interfaces.
- From a PowerShell prompt, start the
dot3svcservice:
Start-Service -Name "dot3svc"- Or from the services console:
Cisco Switch
Finally, we will configure the switch where we will simply declare our RADIUS server, with its IP and the password we defined earlier. We also need to configure its IP.
Manual VLAN assignment
- Configure the switch's IP address:
Cisco# conf t
Cisco(config)# interface vlan 1
Cisco(config-if)# ip address 192.168.1.10 255.255.255.0- Enable
dot1x:
Cisco(config)# dot1x system-auth-control- Declare the RADIUS (NPS) server:
Cisco(config)# !OLD : radius-server host 192.168.1.200 key <password> auth-port 1812 acct-port 1813
Cisco(config)# encrypted radius-server host 192.168.1.200 key <password>- Configure the
gi1/0/1interface:
Cisco(config)# interface gi1/0/1
Cisco(config-if)# switchport mode access
Cisco(config-if)# switchport access vlan 100
Cisco(config-if)# dot1x reauthentication
Cisco(config-if)# dot1x max-login-attempts 5
Cisco(config-if)# dot1x port-control auto- Configure the
gi1/0/2interface:
Cisco(config)# interface gi1/0/2
Cisco(config-if)# switchport mode access
Cisco(config-if)# switchport access vlan 10
Cisco(config-if)# dot1x reauthentication
Cisco(config-if)# dot1x max-login-attempts 5
Cisco(config-if)# dot1x port-control auto- Configure the
gi1/0/24interface:
Cisco(config)# interface gi1/0/24
Cisco(config-if)# switchport mode access
Cisco(config-if)# switchport access vlan 1Automatic VLAN assignment
In a multi-network architecture, automatic VLAN configuration can be an interesting option. It allows you to autoconfigure the VLAN on the switch port according to the user's Active Directory group. See the tutorial “VLAN management on a RADIUS NPS Server with UniFi Access Points” to see how to configure the NPS server.
- Enable
radius-attributesVLAN functionality for interfacesgi1/0/1andgi1/0/2:
Cisco(config)# interface range gi1/0/1,gi1/0/2
Cisco(config-if)# dot1x reauthentication
Cisco(config-if)# dot1x max-login-attempts 5
Cisco(config-if)# dot1x port-control auto
Cisco(config-if)# dot1x radius-attributes vlan